-

How to unblock sites in restrictive countries?
Just moved to a restrictive country like Russia and China and are upset you can’t access your favorite sites? No problem – here’s how to bypass all firewalls.
-
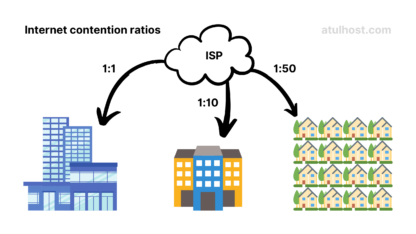
What Is the Contention Ratio?
In the internet world, most of us have heard of the term “contention ratio”. What is it? Why is it killing our internet? We’ll read all those matters that brainstorms in our mind when read…
-

How to check Jio Fiber availability in my area?
Jio Fiber is a revolution in the broadband industry that disrupted the ecosystem of what the other competitors are offering. Of course the service is not available everywhere but Jio is installing and setting up…
-

6 Useful Ways To Reuse an Old Router
If you have an old router, and kept unused, then you can use it for different purposes. You should reuse these things instead of throwing it somewhere because electronic waste is one of the most…
-

Why is a rotating IP address important?
Let us first look at the fundamentals: what is an IP address? An IP address identifies all Internet-connected devices; in addition, it identifies where letters, packs, and other goods should be delivered from our physical…
-
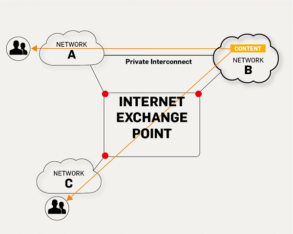
Internet Exchange Point (IXP)
Internet Exchange Points, in short IXPs or IX, is the most critical section of the Internet’s infrastructure. An Internet Exchange Point is a physical facility through which various Internet Service Providers (ISP), Content Delivery Networks…
-
Is 100 Mbps Internet Enough for a Server Rack?
In the world of data centers, servers, and hosting having a faster internet connection is necessary. You shouldn’t be miser here because you could bottleneck everything here. For most of us, 100 Mbps internet connection…
-
Tier 3 Internet Service Providers in India
Tier 3 ISP (Internet Service Provides) are those that take internet connectivity to the last mile. They could be your local cable operator or a broadband service company. Tier 3 ISP buys bandwidth in bulk…
-

Tier 2 Internet Service Providers in India
Tier 2 ISP (Internet Service Providers) plays an important role in distributing internet connectivity from submarine cables to land masses, they can sell their bandwidth to businesses, data centers, enterprises, offices, and even consumers. Since…
-

Tier 1 Internet Service Providers in India
Every country is connected with each other directly or indirectly with the help of submarine fiber optics cables to get access to the Internet. The main job of Tier 1 ISPs is to connect the…
-

How To Make Money Online in India?
If you think the Indian market is a bad paymaster, then you have missed to check the online market yet! Do you have the creative skills, an internet connection and a personal PC? If yes,…
-
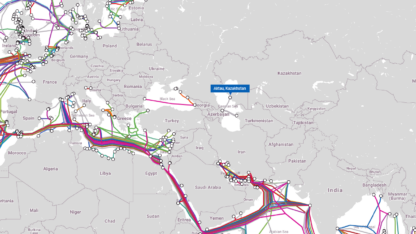
How do landlocked countries get access to the internet?
As you all know we get access to the Internet via fiber optics submarine cables. So how do landlocked countries get access to the Internet as they cannot access the submarine cables that connect other…
Internet
The Internet is a vast network that connects computers all over the world.