Data
-
Navigating the Path to a Master’s Degree in Data Analytics
Key Takeaways: Table of Contents: The Growth of Data Analytics. Data analytics has seen unprecedented growth as businesses increasingly rely on data-driven decision-making. With the advent of big data, industries are investing more resources to…
-

How to Migrate Your Website to a New Host Without Downtime?
Migrating your website to a new host can seem like a daunting task, especially if you’re concerned about downtime. Downtime can lead to lost visitors, revenue, and SEO ranking drops. However, with careful planning and…
-

Why Is Mobile Internet Faster at Night?
Have you ever noticed your mobile internet seems blazing fast at night? If you’re streaming your favorite show or scrolling through social media late into the evening, you’re not imagining things. Your mobile internet really…
-

What Is Object Storage? Use Cases and Benefits
Learn about object storage, a scalable and flexible solution for managing unstructured data. Explore its key features, use cases, and the benefits it offers across industries like cloud applications, media hosting, IoT, and more.
-

SanDisk Extreme Portable SSD: Review
The SanDisk Extreme Portable SSD stands out as a robust and reliable storage solution, tailored for those who require high-speed data transfer and substantial storage capacity in a compact form. This SSD excels in several…
-
Security Concerns for Keyboard Input: Are Third-Party Keyboards Safe To Use?
I often think about different ways big companies collect our data, and one day I started thinking about smartphone’s on screen keyboard. Do they collect our data? In the digital age, our keyboards are the…
-
What Is the 3-2-1 Backup Strategy?
Today, in this digital age where everyone is online, data is one of the most crusial asset for both individuals and businesses. The loss of data, wether due to accident deletion, hardware failure, or cyberattacks,…
-

Does Audience Segmentation Help Increase Leads?
Any business needs to generate a consistent flow of leads to keep growing. However, searching for the right people who are ready to purchase from you is one of the most difficult parts. You can…
-

Server sovereignty: Empowering businesses with digital infrastructure
Introduction to server sovereignty. Server sovereignty has become a cornerstone concept in the digital age, symbolizing an organization’s control and autonomy over its server infrastructure. This concept has evolved significantly with the advancements in technology,…
-
Tech systems for enhanced business performance (maximize revenue)
It’s a bright new day in the world of business, and you’re at the helm, steering your enterprise through the twisted maze of the modern economy. Now, what’s that one thing giving you the edge?…
-

How To Become a Data Analyst?
Are you interested in becoming a data analyst? Do you have a passion for numbers, statistics, and problem-solving? If so, you’ve come to the right place! In this ultimate guide, we will provide you with…
-
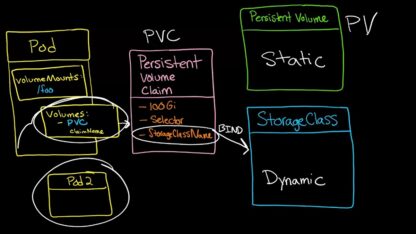
The benefits of using kubernetes persistent volumes in your applications
A persistent volume (PV) is a storage device mounted into Pods. When the Pod is deleted, the content remains on the PV. A PersistentVolumeClaim requests a storage resource that your deployment can claim. It specifies…