Ideal security measures to handle cyber crime, and dealing with it…
Cybercrimes are on the rise, and cybersecurity solutions are growing alongside in order to combat new threats almost daily. In fact, securing your company from online threats is more important than ever, as experts predict total cybercrime costs to reach over two trillion in less than two years.

Nearly as important is how to handle the potential public relations fallout if a company fails to avert an attack in time. To that end, we’ll take you through some of the ways cybersecurity is ramping up efforts to stop these crimes before they start, and the best tips and tricks for handling media relations should the worst happen.
New security measures for cybercrime prevention.
In order to help small and medium businesses combat the looming threats of hacking and other online crimes, companies have improved strategic security standards for the protection of data. One of these belongs to the ISO 27000 family. This is a family of standards that you can utilize to help protect all of the sensitive data that passes through your servers daily. Everything from financial information, to clients’ personal information and beyond, is secured when choosing to adopt this comprehensive system.
ISO 270001 is a standard of security that includes a variety of improved controls for protecting your business and its data from an attack. The standard was updated in 2013 to add more domains of protection than its previous incarnation of nearly a decade earlier. In so doing, cybersecurity experts added new controls aimed at such things as:
- Compulsory information security on all projects
- A prohibition on the installation of unauthorized software
- Proper testing procedures for all software
- Improved risk assessment and management
These improvements serve to further tighten the rigorous controls governing the security of your data and your company; lessening the likelihood of a successful attack.
A systematic approach is key.
As a business, you want to implement the standards and practices that best protect you, your workers and your data at all levels, from the largest variety of threats possible. This is where the 27000 ISO family excels. It offers risk assessments that are deeper than ever before and better security on user access, among other things. The risk of an attack occurring without first being discovered is far less than ever before. Which, as you’ll soon see when we delve into handling the PR surrounding these issues, is of vital importance.
Using aspects of this security family also protects you from a variety of tertiary concerns including, but not limited to:
- Company security policies
- Compliance with any standards
- The physical security of your electronic systems
All of which are important as sometimes we are concerned with a data breach from the outside, but can often fail to realize there are ways to protect our data and physically present systems from the inside, too. A suite of standards such as this takes care of many of these needs successfully, allowing you to redirect your focus to deal with other issues.
How do you handle the fallout if an attack occurs?

Knowing precisely what to do if all security measures somehow do not prevent a breach or loss of data, is the other half of this equation. It is equally as important; while any breach is a major concern, how you choose to handle it in the public eye can make the difference between a mere incident, and irreparable damage to your company’s reputation.
Refer the case of Samsung about Note7 blast and how the company managed its reputation. If they fail to do so, it would result in to a big damage to the trust factor of the company.
Galaxy Note7 (What we discovered) – Samsung’s response on the case.
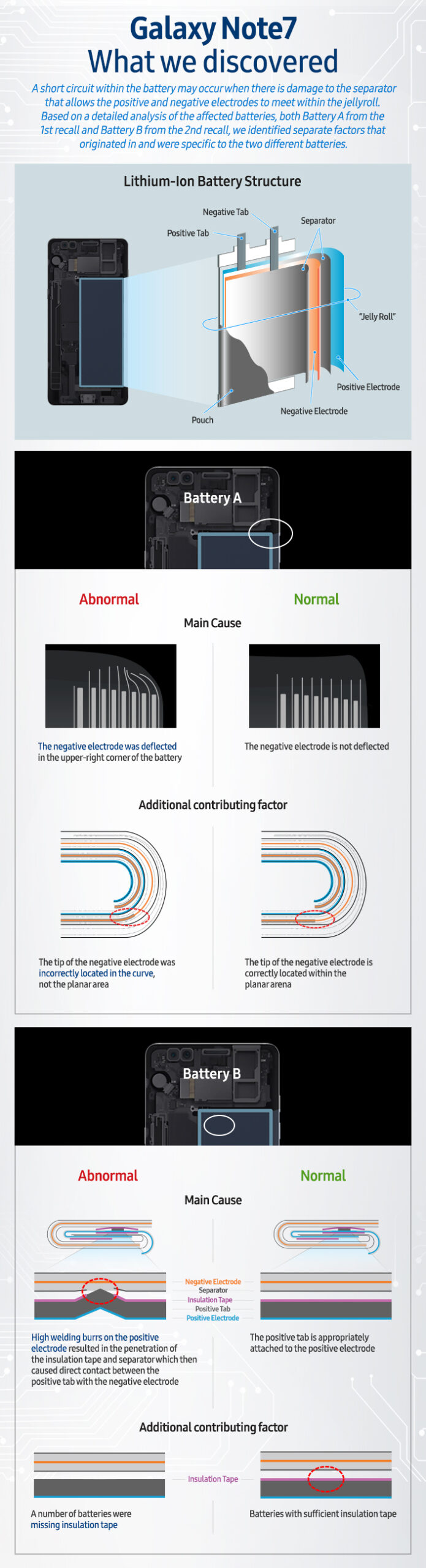
1. Be proactive, not reactive.
It’s a part of best practices not to wait until a crisis occurs before you try to mitigate any damage. In fact, we can see the effects of such short-sightedness even in recent examples.
The already well-known hack on Equifax has shown that not preparing for possible security risks can result in a very real loss of jobs and reputation even at the highest company levels. In fact, some research suggests that a variety of companies place too much confidence in their lackluster abilities to fend off a cyber-attack. This is not a problem you want to have in your company. For one, it lessens the chance that you’ll know what to do if it happens. In addition, it will undermine consumer confidence and possibly lose business, if you don’t handle it well.
So, don’t simply assume you are protected well enough and wait for something to happen. Start early by brainstorming and identifying possible scenarios where key security features are at their weakest and in which hackers could exploit them. You’ll already be one step ahead of negative PR if you identify problems that could happen, and craft statements of reassurance and support beforehand; ideally with the use of data and numbers.
2. Develop a plan with clear guidelines.
It’s best not to assume that everyone will simply use “common sense” when something like this occurs. It’s a nice thought, but it isn’t realistic.
Instead, after you’ve brainstormed possible negative scenarios, come up with detailed guidelines as to how you and your company and employees will deal with each one. Talk things over and decide what the core message to your concerned customers will be. Decide on one person who would be the best choice to deliver that message and answer any queries. Then, make sure everyone else in the team knows how they should respond if the press should ask them any questions, even though they are not front and center. All of this ensures that you and your team are on the same page, and removes ambiguity, thus resulting in less chance of any confusion that could cause a backlash in the press.
3. Don’t wait too long.
For better or worse, we live in the 24-hour news cycle. Any delay might be misinterpreted as confusion, weakness, or an inability to handle a crisis. While you might not need to respond immediately, it’s best to get the ball rolling quickly. Thankfully, since you’ve set up possible scenarios and the rules for dealing with them, you should have no trouble delivering your message in a timely fashion.
4. No excuses, no blames.
One of the worst things companies can do is fumble for reasons to shift blame to third parties in an attempt to absolve themselves. This often gives the appearance of a lack of integrity to both the press and any consumers you may have.
Instead, it’s better to simply admit that the company made an error, despite its best efforts, and let everyone know you are working to correct the issue and do your best to ensure it does not happen in the future. This also prevents you from accidentally misrepresenting the situation; something else you’ll have to deal with later, should it occur.
5. Be up front about resolutions.
The press and consumers like to know the company already has a strong plan for moving forward by the time the chosen representative delivers the core message to the public. To that end, let everyone know how you’re resolving the situation. It isn’t necessary to waste time giving them every single technical detail, but it is helpful to give some basics, and this goes a long way toward restoring any broken trust and keeping your consumers happy.
In summation.
In short, preparing for a potential loss of reputation in your company involves two key components: doing your best with securing your data, and implementing clear plans should a breach happen. Both of these steps involve multiple facets, and addressing each one in turn, clearly, will give you the best chance at not having such issues at all. But it also means that if you do, you’ll be well-prepared and ready to provide concrete, actionable solutions.
Leave a Reply